Backup is King
Everyone should backup their data, especially for a business. Unforeseen events happen and no matter how much you pray, wish or deny, failures happen. I believe in the 3-2-1-0 Rule, regardless of Operating System, Manufacture or Support Contract. This approach helps to answer two important questions: how many backup files should I have and where should I store them?
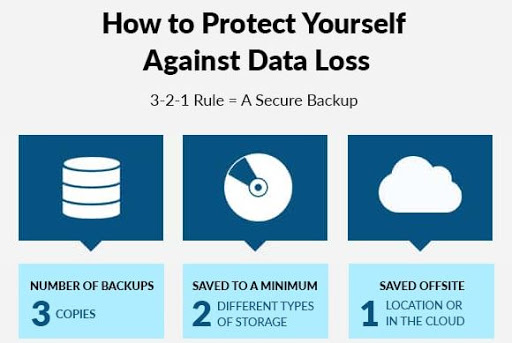
So, what is the 3-2-1-0 Rule?
The 3-2-1 rule became a popular concept thanks to Peter Krogh, a well-known photographer who wrote that there are two groups of people: those who have already had a storage failure and those who will have one in the future. In other words, the 3-2-1 backup rule means you should:
- Have at least three copies of your data.
- Store the copies on two different media.
- Keep one backup copy offsite.
Let’s consider these statements one by one in more details.
1. Have at least three copies of data
By three copies, I mean that in addition to your primary data, you should also have at least two more backups. Why isn’t one backup enough? Imagine that you keep your original data on device #1 and its backup is on device #2. Both devices have the same characteristics, and their failures are statistically independent (they have no common failure causes).
This is why having more copies of your data means you will have less risk of losing data during a disaster. In short, if your data is important to you, be sure to make at least two backup copies.
Note: Another reason to create more than two copies of data is to avoid the situation when the primary copy and its backup are stored in the same physical location.
2. Store the copies on two different media
In the section above, we assumed that there were no common failure causes for all of the devices where you store your data copies. Obviously, this requirement cannot be fulfilled if you save your primary data and its backup in the same place. (For example, disks from the same RAID aren’t statistically independent.) Moreover, it is not uncommon after one disk failure, to experience failure of another disk from the same storage around the same time.
That’s why the 3-2-1 rule suggests that you keep copies of your data on at least two different storage types, such as internal hard disk drives AND removable storage media (tapes, external hard drives, USB drives, SD-cards, CDs, DVDs, or even floppy disks), or on two internal hard disk drives in different storage locations.
3. Keep one backup copy offsite
Physical separation between copies is important. It’s really not a good idea to keep your external storage device in the same room as your production storage. If there was a fire (knock on wood!), you would lose all of your data.
If you work for a company that’s an SMB with no remote or branch offices (ROBO), storing your backups to the cloud might also be an option. And tapes taken offsite are still popular among all company sizes.
The 3-2-1-0 backup rule
The 3-2-1 rule is very general and it works for all data types (individual and corporate) and all environment types (physical and virtual).
When backing up VMware or Hyper-V environments with Veeam, this rule becomes the “3-2-1-0 backup rule” where 0 means “0 errors” during the automatic recoverability verification of every backup
Get In Touch
Share On Social Media
Other Recent Blog Articles
Blackout Blues: Don’t Let Power Outages Fry Your Electronics (Learn From My Fridge Fiasco!)
We’ve all been there. The lights flicker, maybe a surge, and then… darkness. While a temporary power outage might seem like a minor inconvenience, it can actually pose a significant…
Read MoreThe Tariff Tango: How Import Taxes Can Impact Your Computer Gear
In today’s interconnected world, the price tag on your laptop, monitor, or even that trusty keyboard often reflects a global journey of components and assembly. But what happens when governments…
Read MoreFrom Stumptown to Secure Town: Tech Protection for Portland Small Businesses
As a small business owner in the vibrant Portland metro area, you’re likely juggling a million things. From serving your customers to managing your team and keeping a close eye…
Read More